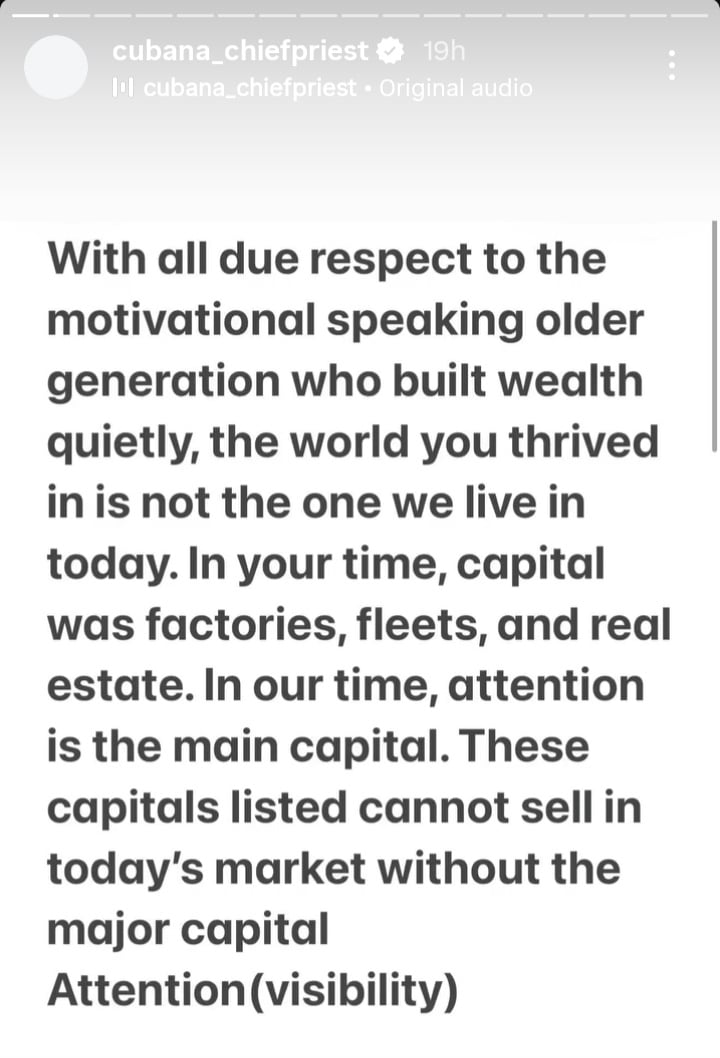
A new version of a known Android banking trojan is making rounds on the internet, stealing sensitive data, and possibly even money, from its victims.
Cybersecurity researchers from NCC Group’s Fox-IT sounded the alarm of a new, upgraded version of the Vultur banking trojan, first spotted in early 2021 but having received a number of important changes and upgrades since then.
While previous versions were being distributed via dropper apps that were smuggled onto the Play Store, this new version uses a combination of smishing and legitimate app abuse. The researchers said that the attackers would first send an SMS message to their victims, warning them of an unauthorized payment transaction and sharing a phone number for the victim to call.
Full takeover
If the victim takes the bait and calls the number, the attacker then persuades them to download a compromised version of the McAfee Security app. While on the surface the app works as intended, in the background it delivers the Brunhilda malware dropper. This dropper drops three payloads, including two APKs and a DEX file which, after obtaining Accessibility Services, establish a connection with the command and control (C2) server, and grant the attackers remote control over the Android device.
For a trojan, Vultur is quite competent. It can record the screen, log keystrokes, and grant the attackers remote access via AlphaVNC and ngrok. Furthermore, it allows the attackers to download and upload files, install apps, delete files, click, scroll, and swipe through the device, and block different apps from running. It can also display custom notifications and disable Keyguard to bypass the lock screen.
Finally, Vultur encrypts its C2 communications to further evade detection.
As usual, the best way to defend against these threats is to use common sense, and only download apps from legitimate, proven repositories.
Via BleepingComputer